Prerequisites
Ubuntu 22.04, Apache 2.4, MySQL 8 and PHP8 on a GCP VM.
Ubuntu 22.04
Enabling Ubuntu auto update
sudo apt install unattended-upgrades
sudo dpkg-reconfigure --priority=low unattended-upgradesChange Default SSH Port
You can change the default SSH port from 22 to something else in sshd_config then restart your sshd service – make sure keep your current SSH connection open until your new port is verified to avoid locked out of your VM. We also need to added the new ssh port to ufw then remove the default 22 from your ufw allow list. For GCP, you need to update the SSH port for using IAP for TCP forwarding.
gcloud compute firewall-rules create allow-ssh-ingress-from-iap \
--direction=INGRESS \
--action=allow \
--rules=tcp:your_new_ssh_port \
--source-ranges=35.235.240.0/20After changing the default SSH port, you need to access your SSH connection by Open in browser window on custom port.
Apache
Disallow Ping Requests
This can be configured in ufw config
sudo pico /etc/ufw/before.rules
change
-A ufw-before-input -p icmp --icmp-type echo-request -j ALLOW
to
-A ufw-before-input -p icmp --icmp-type echo-request -j DROP
Then reload ufw
sudo ufw reloadDisable Apache Signature and ServerTokens
Noticed that in Apache 2.4 these two are defined in security.conf, so change both settings to below and restart Apache2.
ServerTokens Prod
ServerSignature Off
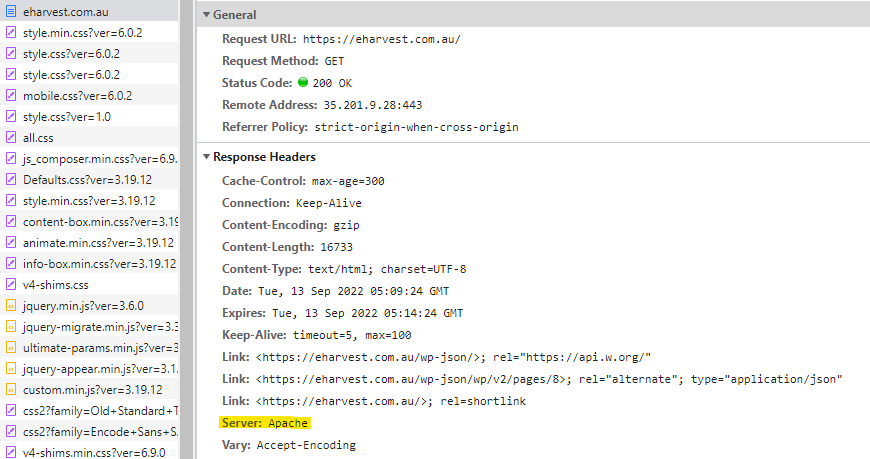
sudo service apache2 restartYou can check in Chrome Console Network tab to ensure the changes take effect.
Disable Directory Browser Listing
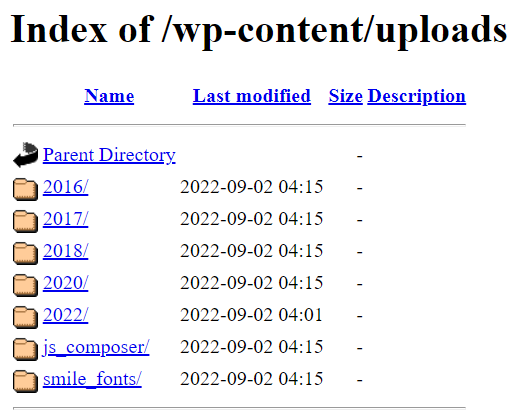
Here is what Directory Browser Listing look like for a WordPress site:
The easiest way to disable Directory browser listing is by changing your site config file from
<Directory /var/www/live/eharvest/public_html/>
Options Indexes FollowSymLinks
AllowOverride All
Require all granted
</Directory>
To
<Directory /var/www/live/eharvest/public_html/>
Options FollowSymLinks
AllowOverride All
Require all granted
</Directory>
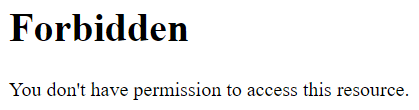
The you’ll see the file listing is prohibited as below:
Run Apache with a non-privileged user
By default your Apache2 installation folder could be running by root. Change it to a non-privileged user such as apache.
# Create apache group and user
groupadd apache
useradd –g apache apache
sudo chown -R apache:apache /etc/apache2
# Add below in apache2.conf file
User apache
Group apache
sudo service apache2 restartDisable phpMyAdmin
Disable
sudo a2disconf phpmyadmin.conf
Enable
sudo a2enconf phpmyadmin.conf
Then reload Apache2Install Fail2Ban
Fail2Ban is a popular open-source intrusion prevention software that provides several advantages for system administrators and website owners, including:
- Protection against brute force attacks: Fail2Ban can detect and block repeated failed login attempts, preventing attackers from guessing passwords or gaining access to sensitive areas of your system or website.
- Reduced risk of unauthorized access: By automatically blocking IP addresses that exhibit suspicious activity, Fail2Ban can significantly reduce the risk of unauthorized access to your system or website.
- Customizable security rules: Fail2Ban allows you to create custom security rules based on your specific needs, providing greater flexibility in detecting and blocking potential threats.
- Enhanced system performance: By reducing the number of failed login attempts and blocking suspicious IP addresses, Fail2Ban can help to reduce system load and improve performance.
- Real-time monitoring and notification: Fail2Ban provides real-time monitoring and notification of security events, allowing you to quickly respond to potential threats and take appropriate action.
Overall, Fail2Ban can significantly enhance the security of your system or website by providing a powerful and customizable tool for detecting and blocking potential threats.
sudo apt-get install fail2ban
sudo systemctl start fail2ban
sudo systemctl enable fail2ban
